Project at a glance 👀
Problem
Curricula offers simulated phishing, but the follow up for learners that fall for simulated phishing is not as helpful as it could be. No matter the situation, all users will go through the same 2 minutes training that repeats information they have already been exposed to.
Approach
I focused on exploring the learners mindset, making sure I understood what would actually be helpful to them while also delivering value to our buyer persona. I quick realized that we could innovate in this area beyond what other solutions have done. This was an opportunity to create another differentiator to make Curricula a market leader.
Goal
- Help learners to not fall for simulated phishes.
- Keep it low effort, quick and easy for the learner
- Validate that they learned something.
- Give admins more insight into whats going on with these people getting phished!
Solution
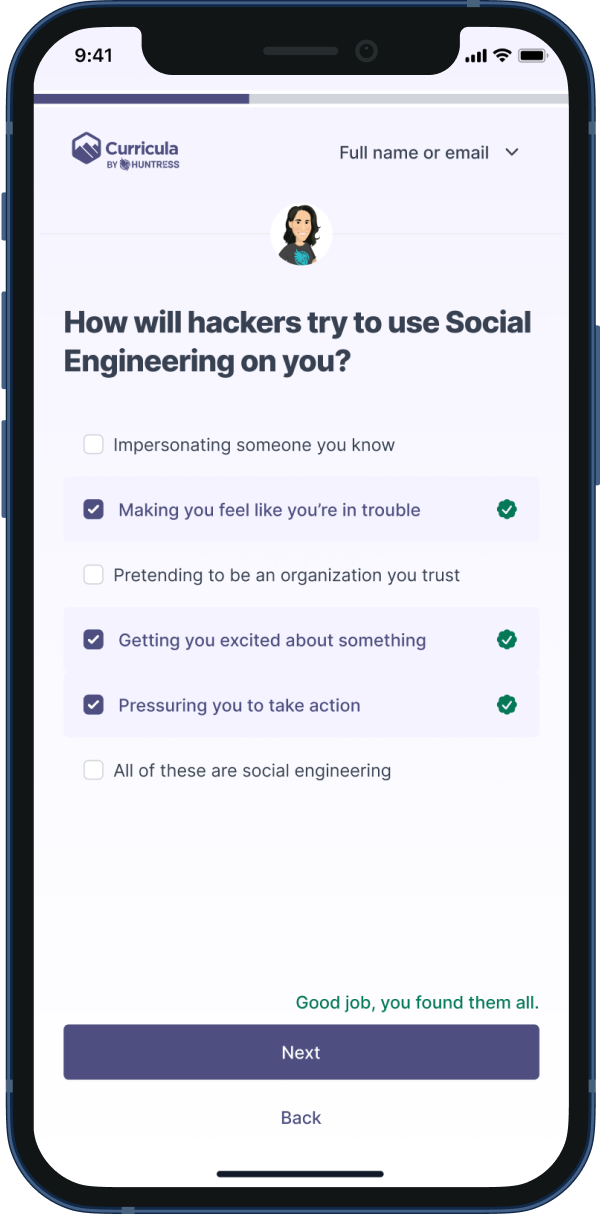
I delivered a new feature called “Phishing Defense Coach” that learners engage with as a response to being phished by the simulated phishing attempt.
In the training learners explore why they failed the simulation. We offer personalized learnings and have a back and forth engagement with the learner.
Through personalization we are able to create valuable data to Huntress, learners, the company admin, and the learners manager to reduce the chance of someone being phished in the future.
Impact
- Learners reported an average preparedness rating of 3.5 out of 5 after completing the training.
- MSP’s felt more confident that they could provide help to those that wanted or needed help.
- Sales leads that were previously apprehensive of switching to a new SAT platform no longer had concerns and were quick to add Curricula to their offerings and become a long term partner.
- Overall, the new Responsive Training feature has significantly improved the user experience of simulated phishing, put more money in my bosses pocket, and is a testament to the importance of UX in the complex world of Cyber Security.
Still here?!? Lets dig deeper...
Company Overview
- For context, Huntress has four core offerings:
- EDR – Managed Endpoint Detection and Response
- MDR – Managed Detection and Response for M365
- SAT – Security Awareness Training
- SIEM – Security information and event management
Im the lead(and only) designer on the SAT platform. All the other products focus on the machines, endpoints and focus on how things are working technically. One of the opportunities with SAT is that we can focus on the end users and not just the technology. By focusing on our users mental modals, mentality and the reasoning behind the behavior, I believe we can start bringing in actionable insights to help improve security awareness and help reduce the required vigilance to stay ahead of threat actors. Thats the high level behind a lot of my actions, ill start digging into the details now.
Primary Collaborators
- 1 Principal Group Product Owner*
- 1 Engineering Manager*
- 1 Senior Product Designer(me)*
- 1 Principal Full Stack Engineer
- 1 Staff Full Stack Engineer
- 1 Senior UX Technical Writer
- 2 Senior Full Stack Engineers
- * = Product trio
Process Overview
The design process is not always linear. To have success, I depend on feedback loops, keeping the team informed, and always in a position to get feedback quickly from stakeholders and users. The logic behind the process is to build confidence that we building the right solution for our users.
Initial Problem & Vision
The experience that learners go through after being phished feels incomplete. It was fine as an MVP several years ago to get the product to market, but its time to create a premium experience that further addresses our users needs(both partners and learners). From a tech perspective, we want to be able to track learners progress through simulations more closely. From a UX perspective, we want to better understand the needs of partners and learners. For learners, we already know that we want to provide a more personalized approach. For partners we already know that we want to give them more insight into the simulated phishing interactions, enable them to make more informed decisions, save time, and reduce the required effort to complete the tasks they have related to this process.
This could be an opportunity to create something unique to our platform for both learners and partners.
MSP Partner
Example User

Bio
Federico is a technician at a medium-sized managed service provider (MSP). He manages Security Awareness Training for all 13 of the MSPs clients, which include medical offices, bakeries, hotels, and apartment buildings.
Demographics
Work
Duties
Job Roles
IT
- Directors
- SysAdmins (set up & training techs)
- Technicians
Companies
Motivations
Customer compliance requirements for:
- Healthcare
- Financial Services
- any other industry with compliance reqs
Frustrations
Redacted persona for our Partner / Admin
Understanding the Space & Users
This is where the discovery work really gets fun. We have assumptions, ideas, and varying levels of understanding that created our hypothesis. The goal of this stage is about being smart and strategic with your team’s efforts by identifying and testing these assumptions upfront, rather than learning the hard way later on.
We had a lot of assumptions that we were unsure of when thinking about the outcomes our partners needed. Luckily, we had some amazing stakeholders and partners that were eager to give feedback.
I conducted six one-one user interviews with partners across the US that had a good mix of needs to ensure we had a good source of data. During these 45-minute calls i started with a generative approach, trying to understand what problems they were facing. If I felt like we were already aware of the problem they were facing, i would pull up the experience i mocked up and get feedback. If I felt like they were showing me a problem that was new, i would dig in deeper to help me understand the needs they had.
I also worked with internal stakeholders that were able to provide different perspectives outside of the product trio. Some helped give me insight on competitors, accessibility concerns with the solutions proposed so far and it was a chance for others to deepen my understanding of this problem.
Key insights from user interviews(that i can share):
- Admins have to keep track and take action with each and every learner that is phished.
- There needs to be an automated solution to the problem of “one of my learners have been phished, i have to figure out who to talk to, reach out to them, and have a conversation about phishing.”
- The only measurement for simulated phishing is “compromise rate”.
- We need to surface meaningful metrics for our admins.
- Other platforms show a video to phished learners, but don’t really know if its helping.
- There needs to be a meaningful engagement with the learner, not just a video that complies with insurance requirements, we want to go beyond “watch this” and into “Lets learn something together!”
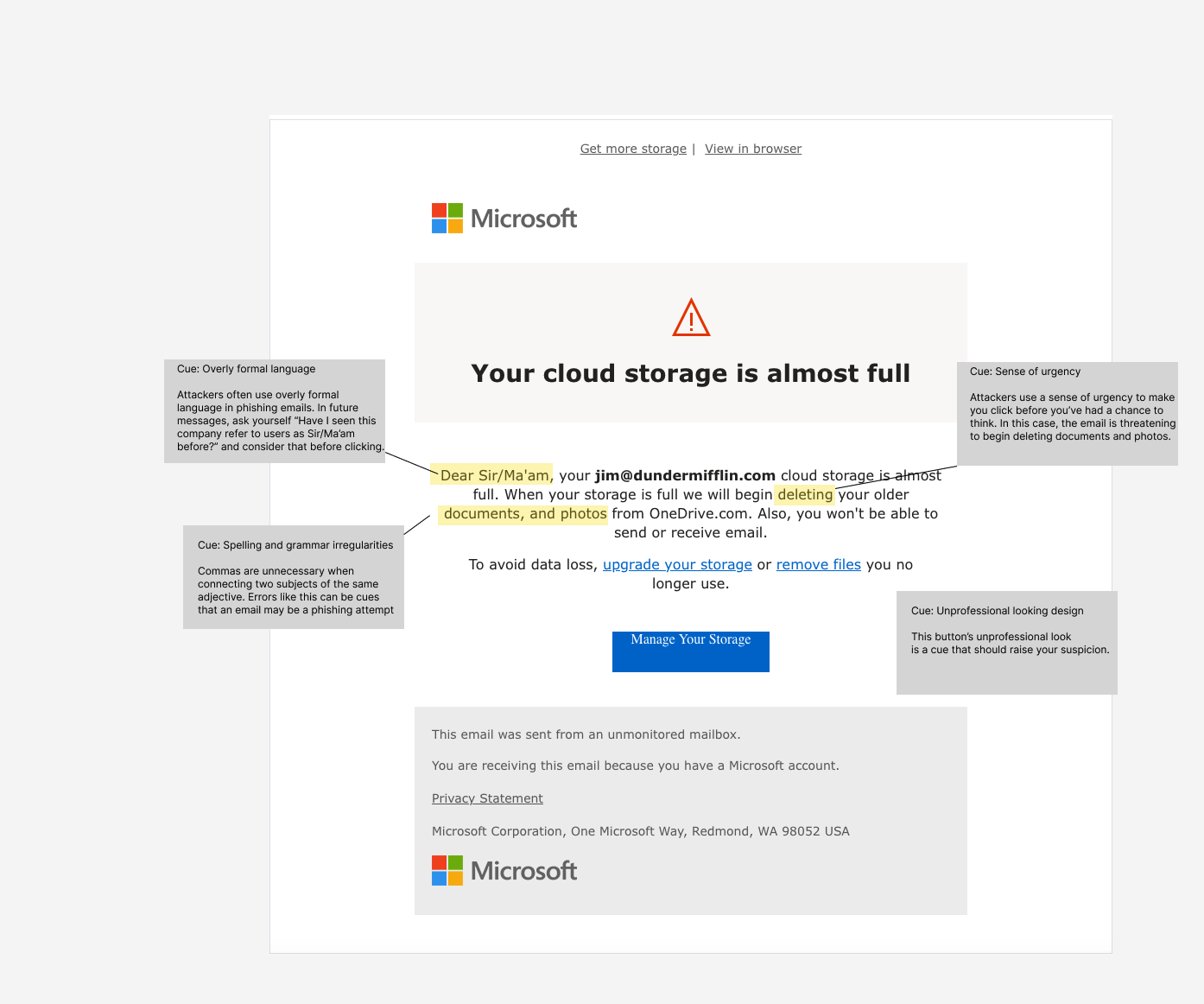
This is the original understanding of what we wanted to teach. We see the high fidelity version of this as an industry standard. So we asked ourselves, “How can we create a differentiator?”
These are several of the concepts I iterated on during the first phases of the project to help us imagine the possibilities of what we could do.
Strategy & Planning
We are now able to narrow down the type of experience that our partners and learners will benefit from.
High level goals(that i can share):
- There needs to be an automated solution to the problem of “one of my learners have been phished, i have to figure out who to talk to, reach out to them, and have a conversation about phishing.”
- We need to surface meaningful metrics for our admins.
- There needs to be a meaningful engagement with the learner, not just a video that complies with insurance requirements, we want to go beyond “watch this,” and into “lets learn something together.”
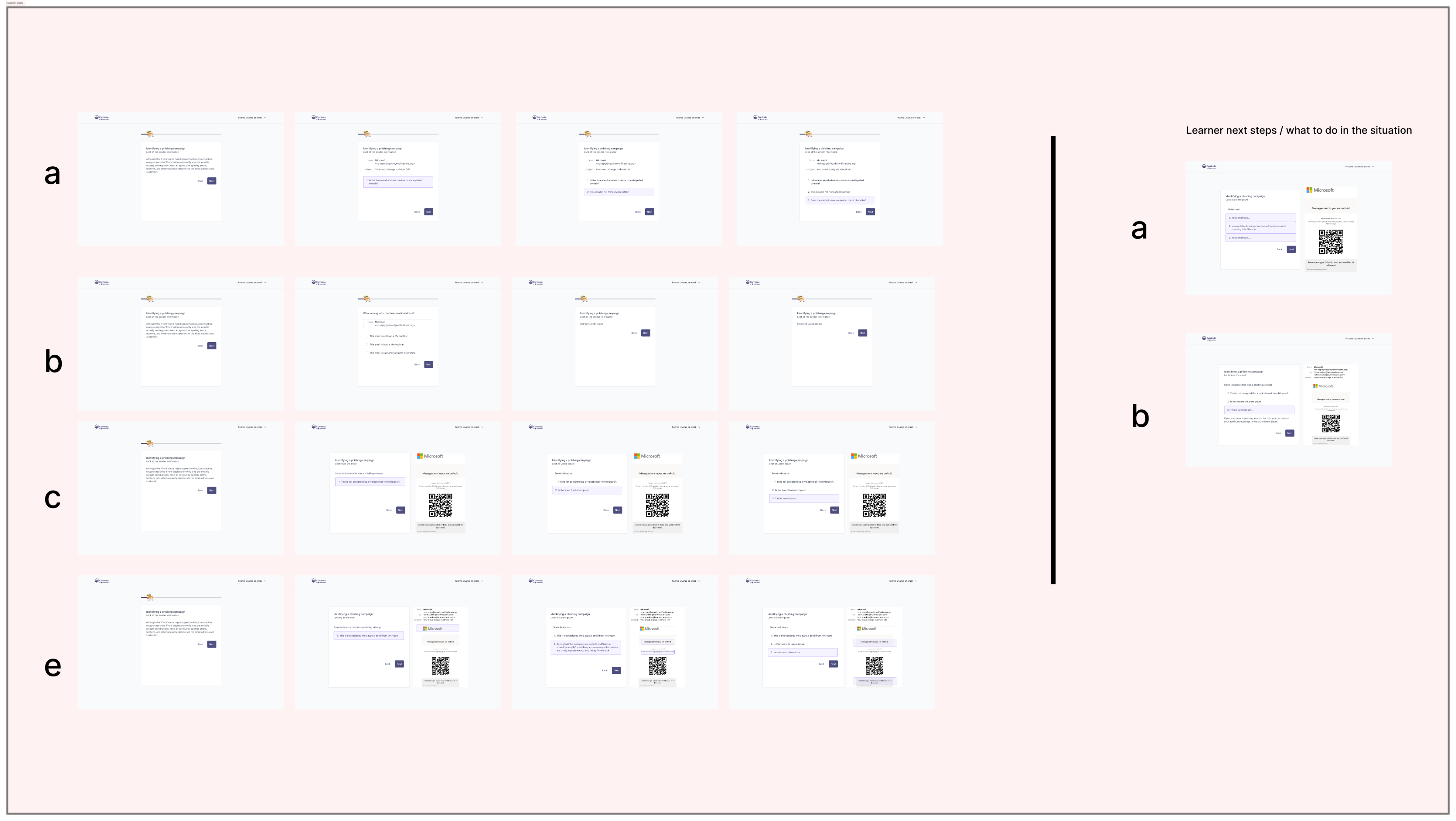
Some flows, layouts, and concepts presented to the product trio now that we have a better understanding of our timeline, capabilities and limitations.
Solutions
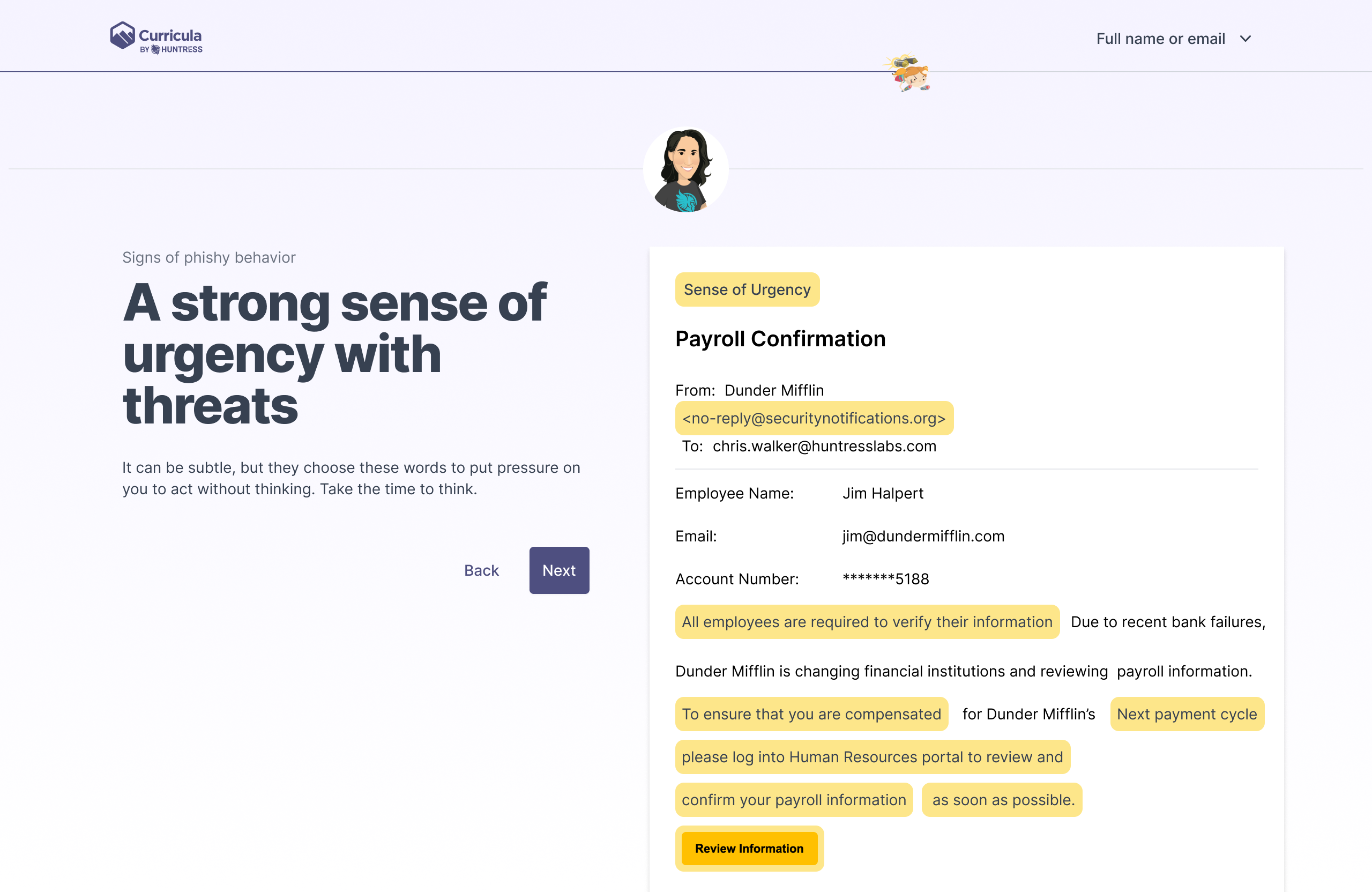
The effort on this was too high for an MVP version. The main issue was the ability to select and tag areas in the email. Our email builder would have to be rebuilt for us to accomplish this design.
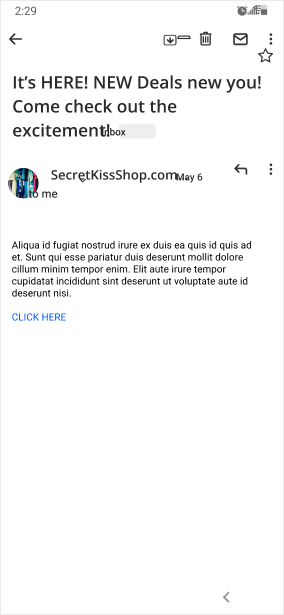



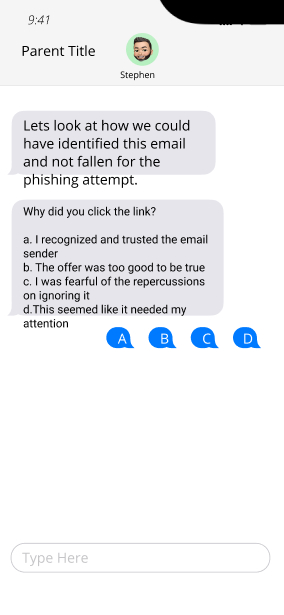
A conversational approach to engage our learners.
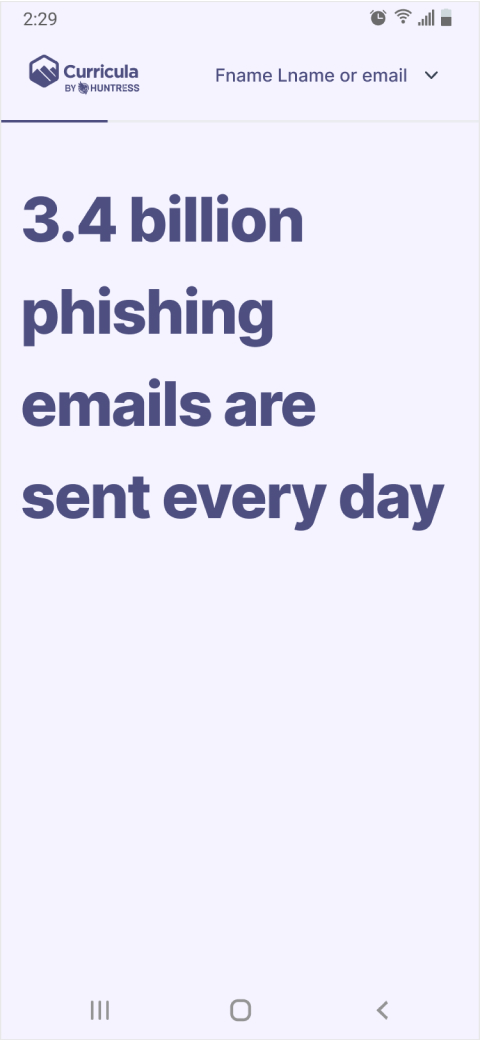
Adding in quick facts to keep the learner engaged, hopefully adding a little bit of “wow, thats interesting.”
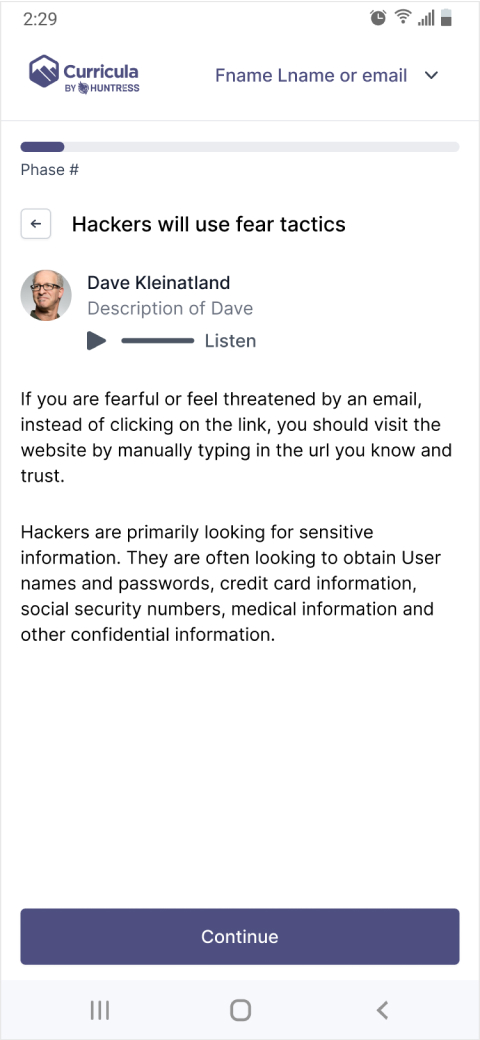
Ability to be engaged via audio to avoid requiring too much reading from the learner.
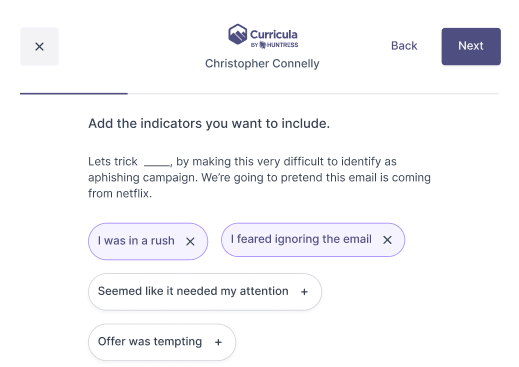

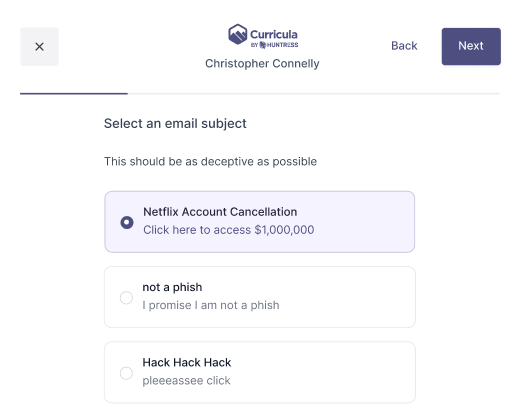

My personal favorite, learn by doing! With this approach the learner would create a phishing campaign and send it to either themselves, the account admin, or another learner.
Deliver
In the end we decided to go with a coach style experience that helps learners based on the simulated phish they received, and the reason they fell for the phishing campaign. The final step is a “health check” that enables their admin to engage with learners that may still need more guidance.
User feedback
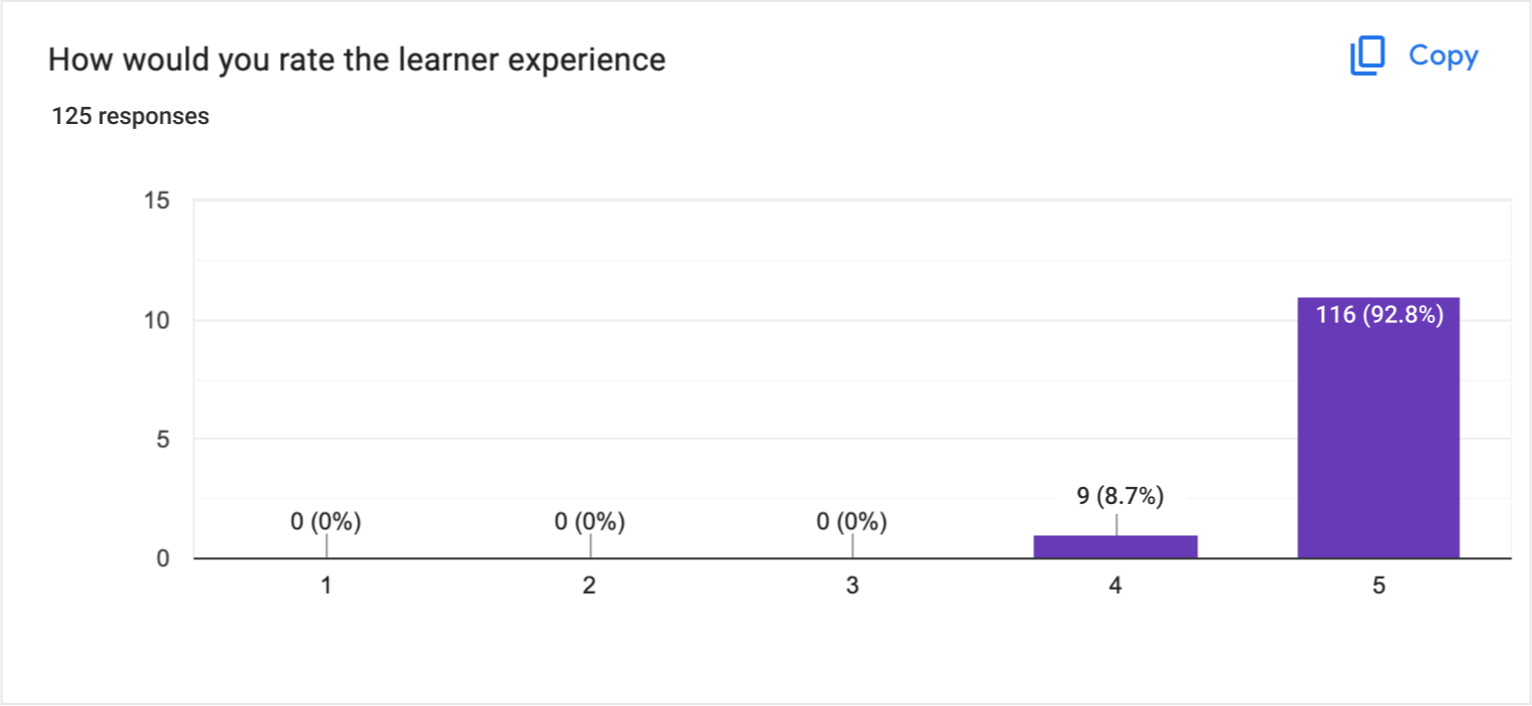
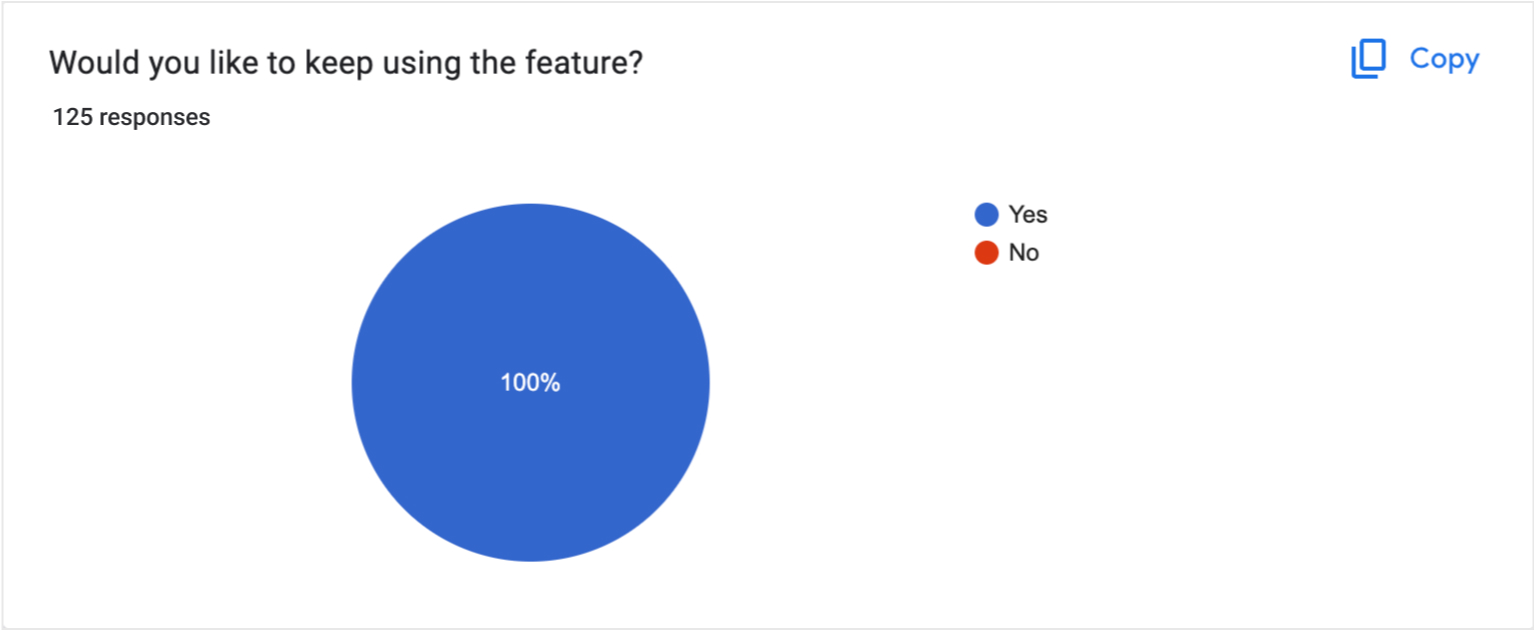
Positive feedback from our first group of users this feature was released to.
Internal Feedback
Positive feedback from the Founder-CEO
Positive feedback when I announced the feature to the product org.